top of page
Techmaniac


Top 21 Hacking Gadgets Revealed
Hacking gadgets, or tools used by hackers to gain unauthorized access to systems, are a controversial topic due to their potential for...
Tutorials Freak
Feb 24, 20242 min read

Exploring the Top 10 Hacker Operating Systems
In the realm of cybersecurity and ethical hacking, the choice of an operating system can significantly impact a hacker's ability to...
Tutorials Freak
Dec 9, 20232 min read


Exploring the Growing Demand for Ethical Hackers in India
In the rapidly evolving landscape of cybersecurity, the demand for ethical hackers, also known as white-hat hackers or penetration...
Tutorials Freak
Nov 27, 20233 min read


Why You Are Doing Automation Wrong in Ethical Hacking
Automation is a powerful tool that can be used to automate many tasks, including ethical hacking. However, it is important to use...
Tutorials Freak
Nov 16, 20232 min read


Vulnerability Assessment in Ethical Hacking: Identifying and Prioritizing Security Weaknesses
In the realm of cybersecurity, vulnerability assessment plays a crucial role in identifying, classifying, and prioritizing...
Tutorials Freak
Nov 8, 20232 min read


How to prepare for CTF Competitions
To prepare for Capture the Flag (CTF) hacking competitions, you need to have a strong foundation in ethical hacking and cybersecurity....
Tutorials Freak
Oct 24, 20233 min read


How long does it take to learn ethical hacking?
In the ever-evolving world of cybersecurity, there is an increasing demand for skilled professionals who can safeguard digital landscapes...
Tutorials Freak
Oct 18, 20233 min read


Difference between Penetration Testing and Ethical Hacking
In the world of cybersecurity, two terms frequently used interchangeably are "penetration testing" and "ethical hacking." Both are...
Tutorials Freak
Oct 14, 20233 min read


Top Ethical Hacking Forums for Cybersecurity Enthusiasts
Ethical hacking, often referred to as penetration testing or white-hat hacking, plays a crucial role in identifying and mitigating...
Tutorials Freak
Oct 5, 20233 min read


Is CEH Certification Necessary for Ethical Hacking Jobs?
Ethical hacking, also known as penetration testing or white-hat hacking, is a critical component of cybersecurity. Ethical hackers use...
Tutorials Freak
Sep 27, 20233 min read


Exploring Ethical Hacking: The Quest for a Perfect Solution
Ethical hacking, also known as penetration testing or white hat hacking, involves the deliberate probing of computer systems and networks...
Tutorials Freak
Sep 22, 20233 min read


What's it like to be an ethical hacker?
In a world where digital threats loom around every corner, the role of an ethical hacker has become more critical than ever before. These...
Tutorials Freak
Aug 25, 20233 min read


Essential Tools and Technologies for Ethical Hackers: A Comprehensive Overview
Ethical hacking, also known as penetration testing or white hat hacking, involves conducting authorized security assessments to identify...
Tutorials Freak
May 22, 20232 min read

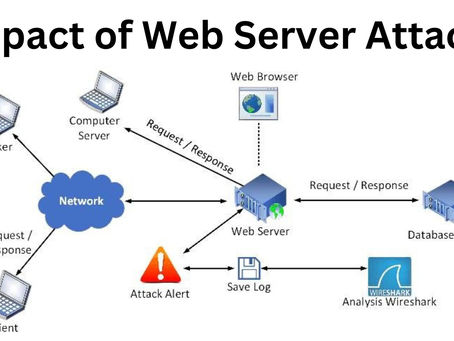
Impact of Web Server Attacks
Web server attacks have become increasingly common in recent years, with hackers using sophisticated methods to breach websites and steal...
Tutorials Freak
Apr 19, 20233 min read


10 Different Types Of Hackers
There Are Ten Types Of Hackers. A hacker is any proficient computer expert who uses their technical expertise to solve a problem....
Tutorials Freak
Nov 3, 20224 min read


What Is Hacking | Common Types of Hacking
Hacking is the action of exploiting security flaws in a network and a knowledge processing system to get access to private or company...
Tutorials Freak
Jul 22, 20223 min read
bottom of page